Recently, I have been taking part in the third edition of the Cyberskiller Challenge cybersecurity competition. Last year, I have managed to get third place, we will see how will I perform this time around. The competition consists out of three stages: school team qualifications, provinces-wide eliminations and the country-wide finale. This writeup refers to the first stage.
First, there was a multiple choice quiz (which was identical to the last year’s, by the way). It was quite easy, considering that most of the answers were included in a handbook available on the website for complete beginners. However, this year’s new introduction of practical tasks as soon as the first stage is very welcome, even if almost all of them were insultingly simple; just run a specific Linux command, or write three lines of python or SQL. I didn’t have many problems completing them all. However, two of them caught my attention, and I have decided to break them down below.
“Switching Bytes”
The first 100 bytes of the file provided here have been switched in pairs with each other. The goal is to recover the file, decompress and run the binary to get the flag.
This is my solution:
# by viberunner
with open("reversed.gz", mode="rb") as file:
contents = file.read()
arr = bytearray(contents)
buffer = None
for i in range(len(arr)):
if i < 50:
buffer = arr[(i*2)+1]
arr[(i*2)+1] = arr[i*2]
arr[i*2] = buffer
with open("out", mode='wb') as outfile:
outfile.write(arr)
Personally I haven’t written scripts, that modify files on the byte level before, so this one challenge was particularly enjoyable for me. The script above makes an array of all bytes of the file, and then systematically switches them around in pairs (just as per the chall description). I had fun writing this simple program…
“Custom Webserver Config”
…which I cannot say about this challenge. Objective was to track down the specific error log of an apache2 webserver on a Linux box, having access to an user account. The flag was hidden in the log file, and the webserver was running as root. However, I have spent way too long throwing all the tricks in the book against the wall, and nothing worked. I have carefully read all of the config files, analyzed environment variables, dug through everything I could find, to no avail. Almost having lost all hope of acing all challenges, I have remembered about a nifty tool known as pspy. It allows you to spy on all of the processes, even without root. And sure enough, having uploaded the binary to the machine, running it with the “-f” flag, and launching a website fuzzing tool to get a bunch of 403 errors, we got the location of the log file!
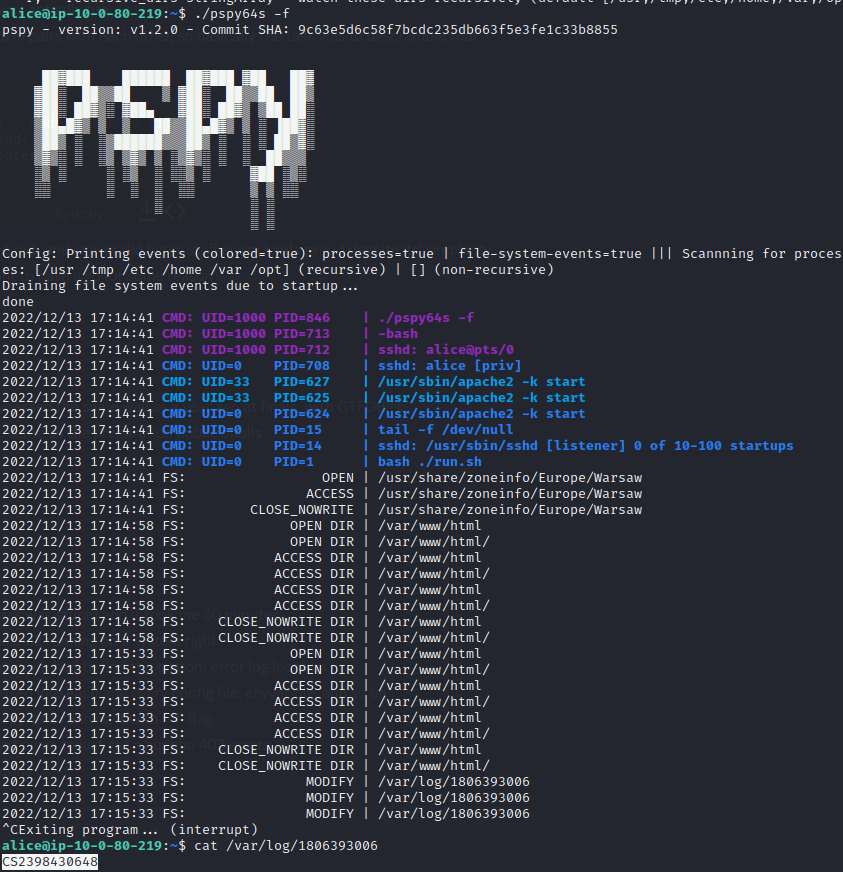
It’s probably worth mentioning, that I couldn’t just simply list the log files inside /var/log, because of the hardened permissions.
Conclusion
Despite the challenges being aimed at complete novices, I did have an enjoyable time solving them. I am looking forward to the second stage of the competition in March. It will certainly be interesting, as I will be competing as a lone wolf against 3-people teams. Until next time.