This post is a continuation of the series of writeups from the second stage of the competition CyberSkiller Challenge Poland III Edition.
Writeup for the day one: link
===== Task 6, 20 points =====
Task description translation:
Do you understand SSL certificates? How about certification paths? You will find the answer to this task inside the Certification Authority. Beware of the long queues to the desk, though!
[Provided: SSH credentials]
Funnily enough, this very task was included in the finals last year.
Looking around common paths, where SSL certs are stored is fruitless, as there is nothing noteworthy in /etc/ssl/certs.
However, if you run ps aux, you can see webservers running… how about we take a look at them?
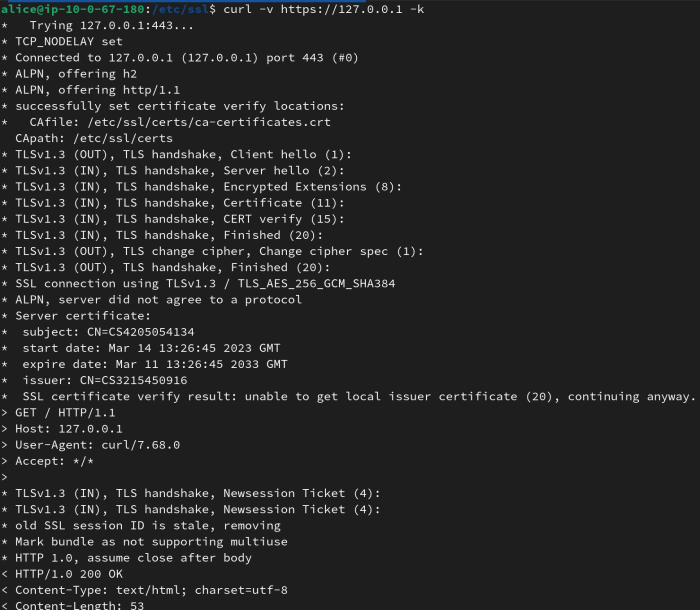
Yes, the flag is (one of the) simply included in the SSL certificate of a webserver running on localhost. I wasted so much time digging around the files, but whatever.
===== Task 7, 10 points =====
This one was very straight-forward, just connect via NCAT and paste your GPG public key. Then, decrypt what you get back. I mean, this is basically the same what the description said anyway…
===== Task 8, 20 points =====
Task details found on the machine website and in task description:
Hint offset = 243
9SS54591C85267C879
Yep, this is all you get in this one. I could not figure this one out myself within the 45 minutes. After all, it’s not really clear what could possibly this even mean…
However, after this stage was over, I wrote to the organizers asking for the solution. Here is what they wrote back (translated):
In task 8 you had to read the index from the hint, under which the second answer is located and ask the server for this range using Range headers.
Yeah, that didn’t make things much clearer. However, I assume you had to send specific requests to the webserver using the Range header, so it was not just a deciphering/decoding challenge, but rather a web one?
===== Task 9, 30 points =====
Task description translation:
Login to the system via SSH. There is a CUPS daemon running, to which a printing order is being sent every minute using an unknown protocol.
Intercept the print order utilizing available tools, identify the protocol and analyze the traffic, in which the answer is being sent.
The print order might require additional conversion, to receive the answer. You are able to use the Virt printer, which prints to the /var/spool/cups-pdf/alice/ directory.
[Provided: SSH credentials]
This is yet another challenge which was listed on last year’s finals.
Just log in, abuse tcpdump as usual, and the answer is hidden in the image file /root/test.png:
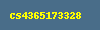
But if you really like playing by the rules, my assumption is, that the intended way to solve this was to intercept the print order, analyze the packets’ data format, and convert the attached bytes to an image file.
===== Task 10, 20 points =====
Task description translation:
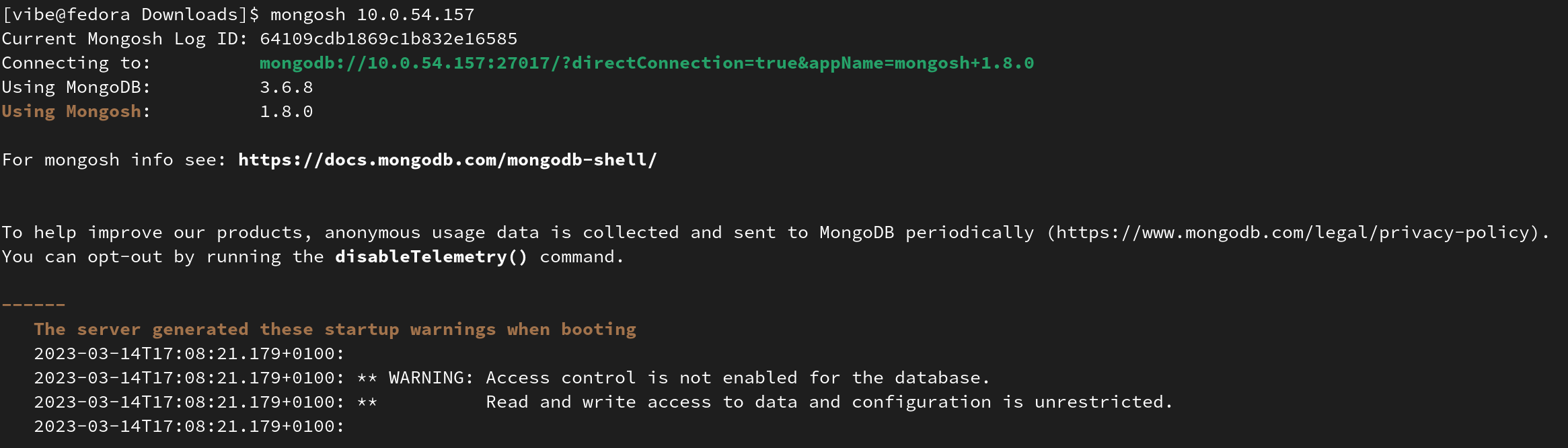
You have access to a server handling a MongoDB database. Server is available under [MACHINE IP].
Utilizing client tools designed for MongoDB, connect to the insecure server and obtain the answer from the right collection.
Yes, it’s enough to download mongosh, read the documentation and basically just read the flag, since the access control has been disabled. Pictures below depict queries used to complete this task:
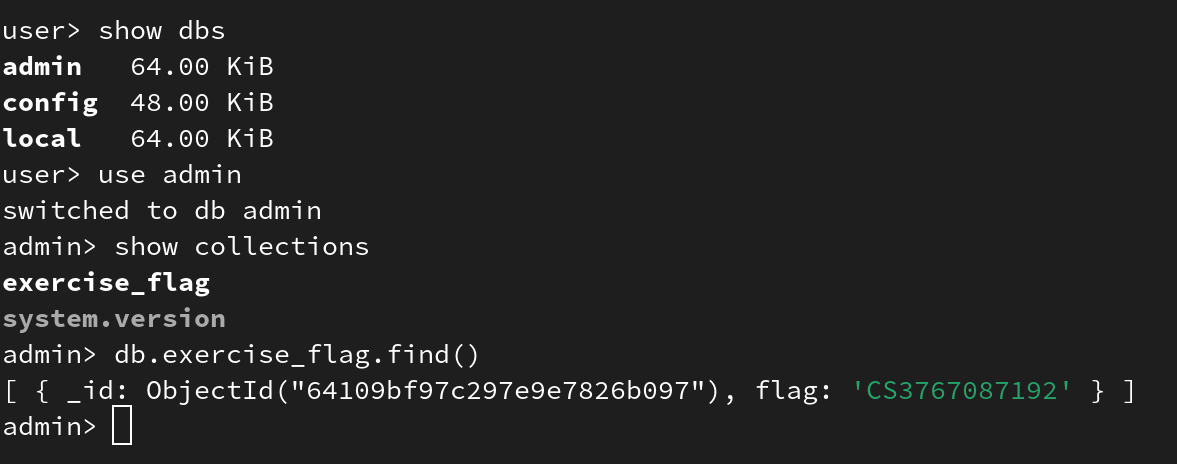
===== Conclusion =====
This day wasn’t particularly exciting, was it…
However, the next day had at least one cool challenge: link